In this article, we explain different kinds of topologies in both wired and wireless networks. We will also have a brief look at different types of networks and IOT supporting technologies.
Different topologies in Wired network
The topologies of star, ring, mesh and bus vary in appearance and operation. In terms of networks, some don’t even exist anymore. Let’s have a look at what we’ve got.
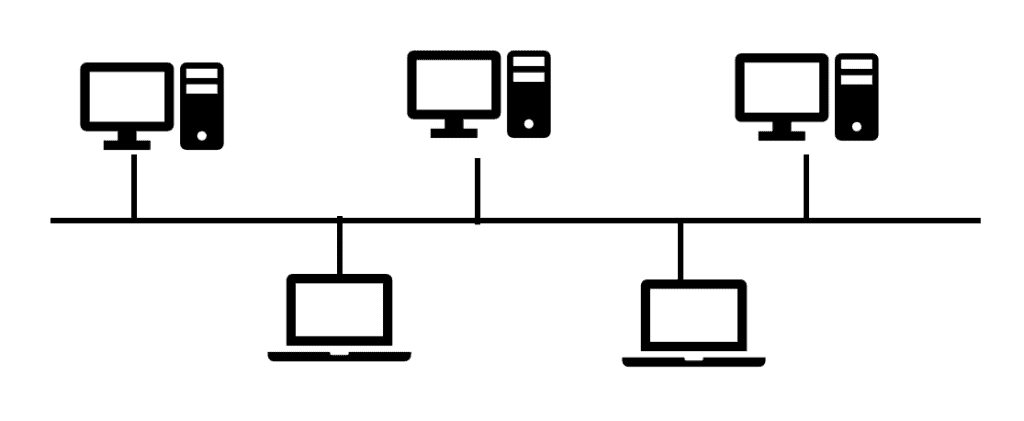
Bus Topology Network
Everything was connected to a single lengthy wire. A primary cable trunk was utilised in a bus topology.
Ring Topology Network
All computer systems were linked in a full loop in a real ring topology.
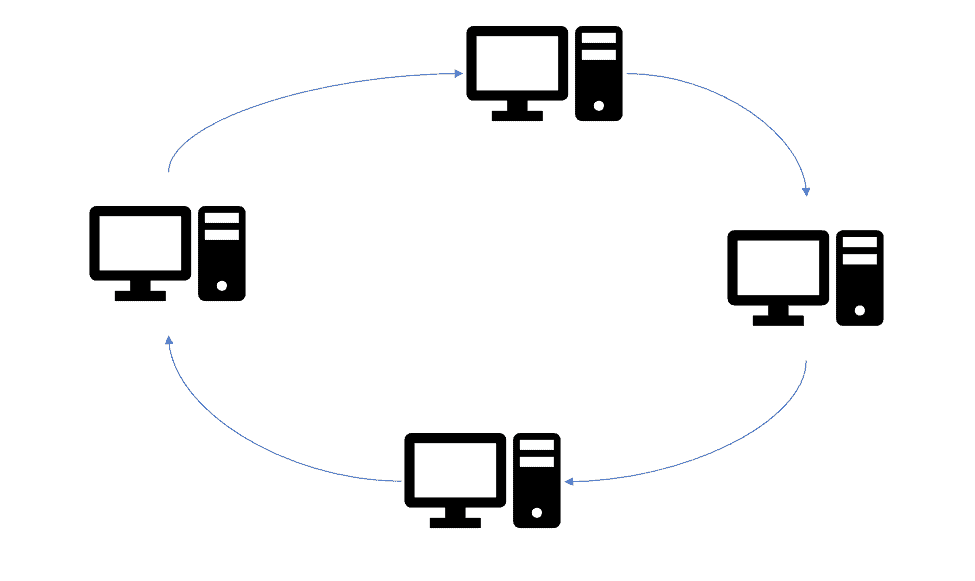
The deterministic mode of communication was the key selling point for ring networks. When it was their time, the devices on the ring played well and accessed the ring.
Between bus and ring networks, data moved in various ways, resulting in distinct issues and solutions. Data from each computer on a bus topology network was simply broadcast to the whole bus.
To prevent a signal received from one computer from reflecting at the ends of the cable and shutting the network down rapidly, a network utilising a bus architecture required termination at either end of the cable.
Topologies are diagrams, similar to circuit diagrams in electrical engineering. Real network cabling does not follow perfectly straight lines or circles.
Data traffic on a ring topology network, on the other hand, flowed in a circle in the same direction from one computer to the next. Ring networks do not need termination since the cable has no terminus.
The same issue existed in both bus and ring topology networks: if a cable broke at any point, the whole network would cease operating. The broken endpoints of a bus topology network lacked the essential termination, causing reflection between still-connected machines. A ring topology network break simply severed the circuit, halting data transmission.
Star Topology Network
All of the computers in the network are connected to a central connection box in the star architecture.
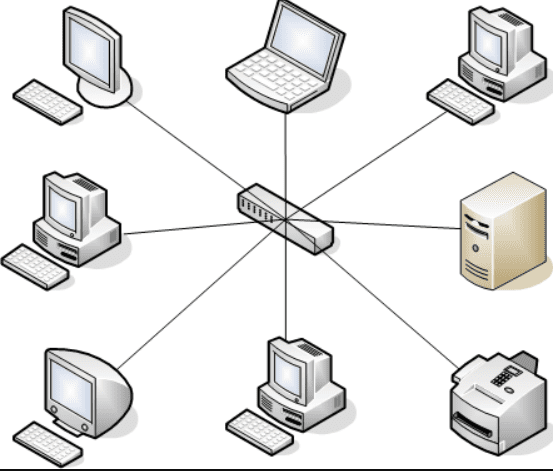
Star topologies have a significant advantage over ring and bus topologies in that they provide fault tolerance—if one of the connections fails, the other computers can still communicate.
In a star topology, a damaged cable only affects the machine to which it is attached.
The old-style star topology networks, on the other hand, were not particularly successful since bus and ring topology networks were popular and easy to install. Existing networks could not readily be redesigned to adopt a star topology by network hardware designers.
Despite the fact that network designers couldn’t simply employ a star topology, the advantages of star topologies were so compelling that clever individuals devised a way to use them without needing a significant redesign—and the method they devised was brilliant.
The designers of the ring topology network struck first, reducing the whole ring into a compact box known as a multistation access unit (MAU).
This was immediately followed by the people who worked on bus topology, who reduced their bus (also known as the segment) into their own box, which they named a hub.
Physical vs. Logical Topologies
The topologies constructed with an MAU and a hub seemed to be a star topology on the surface, but when seen as an electrical schematic, the signals operated like a ring or a bus.
The prior concept of topology clearly needs to be clarified. That’s why we have two terms for how the connections appear physically, physical topology, and logical topology, which describes how the signals go electrically.
A hybrid topology is any networking technique that blends a physical topology with a logical structure. Since the dawn of networking, hybrid topologies have come and gone.
Only two hybrid topologies, star-ring and star-bus, have ever achieved any level of popularity. Star-ring eventually lost market share, while star-bus now reigns supreme among topologies.
Devices on today’s networks are only connected in a star topology and link to a central box known as a switch.
Mesh Topology
The wired mesh architecture has many connections connecting each node, allowing for numerous pathways between any two nodes. Because it needs so many individual lines, the wired mesh architecture is seldom, if ever, encountered in LANs.
A partial mesh, on the other hand, is used to link networks. A mesh topology may be defined as a collection of interconnected networks that have more than one feasible data channel between network sites.
The amount of fault tolerance improves as the number of routes connecting networks grows because mesh topologies offer many pathways between networks.
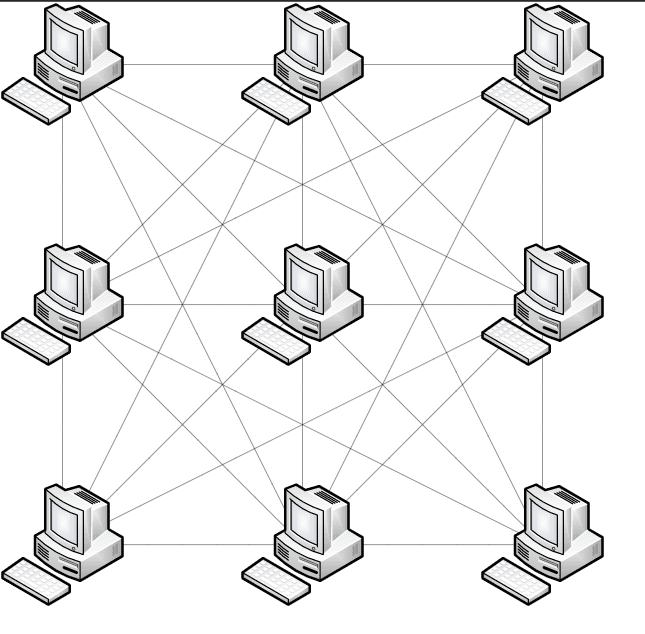
In an office, you won’t find partial mesh networks. The word is most often used to describe links between networks across long distances, such as on a university campus. Outside of the CompTIA Network+ test, you won’t see a complete mesh network at all.
Wireless Topologies

Topologies aren’t just for wired networks. Wireless networks also need topologies to get data from one machine to another, but using radio waves instead of cables involves somewhat different topologies.
Wireless Mesh Topology
Every device in a wireless mesh topology network communicates with each other through two or more wireless access points (WAPs). Some paths between two devices may need passing via another mesh network member.
Wireless ad hoc network
Wireless networks may run in one of two modes (compTIA calls these topologies): ad hoc or infrastructure. The wireless nodes in an ad hoc mode network connect directly with each other; no WAP is required for two hosts to interact.
While this is useful for sharing data between two computers at the train station, ad hoc 802.11 networking will not allow you to connect to your workplace network or the Internet.
Infrastructure mode, which employs a WAP device, is required to connect to an existing wired network. The WAP connects to the wired network and transmits data between wireless clients and wired network services.
Types of Networks
Networks occur in a variety of sizes and have varying numbers of machines connected to them. Some individuals utilise the smallest network possible to link two computers in their home so that they may exchange files or play games together.
Consider a company with thousands of workers in dozens of countries that need to connect their laptops to complete work. Most networks are classified as LANs or WANs by network experts. There are a few additional groups as well.
LAN ( local area network )
A local area network (LAN) is a network that spans a limited area and has a small number of machines. A LAN is generally located in a single building or a group of buildings nearby.
Home and school networks are examples of typical LANs. A local area network (LAN) is just a single network or broadcast domain made up of nodes that can hear each other’s broadcast broadcasts. Broadcasts are never forwarded by routers.
WAN ( wide area network )
A wide area network (WAN) connects a large number of computers across a vast region. A WAN is made up of two or more LANs that are linked together.
A WAN is formed when all of the LANs in a city school district, for example, are linked together. In a WAN, computers are generally connected through a public network, such as a phone system, leased lines, or satellites.
The Internet is the greatest WAN in existence, since it is a global network that links billions of devices from various networks.
MAN ( metropolitan area network )
A metropolitan area network (MAN) is a collection of networks linked over a shorter distance than a wide area network (WAN), such as a network of local government offices in a town or city.
MANs might be as little as a few city blocks or as large as whole cities. A MAN’s sites are often linked through fiber-optic cable or another high-speed digital circuit, and the MAN itself may handle both voice and data traffic.
SAN ( storage area network )
A storage area network (SAN) is a server that may expose a pool of hard drives as any number of logical discs across the network. It offers a client machine with an interface that looks like a hard drive and allows the client’s operating system to read and write blocks across a network.
WLAN
What do you name your neighbourhood coffee shop’s network? Although it is a local area network (LAN), regular users will not be able to connect their laptops to it. As a result, it’s a wireless LAN (WLAN). The important thing to remember is that a WLAN will always be a WiFi 802.11-based network capable of serving multiple clients.
PAN
Consider all of the gadgets you may be carrying that communicate with one another. Your smartphone and laptop or tablet may be able to converse. What about a smartphone that connects to a wristwatch?
These are instances of a PAN (personal area network), which is a collection of gadgets on or near your person that exchange network data traffic. Furthermore, a PAN allows one device to connect to a LAN or even the Internet on behalf of all other devices.
WPAN (wireless personal area network) is a subtype of PAN. WPAN (wireless personal area network) is a PAN that employs technologies such as Bluetooth and infrared (IR) to build a single point-to-point connection across extremely small distances. Bluetooth connections may range from 100 metres for the strongest Bluetooth connections to 5 cm for NFC (near field communication) devices.
The distinction between LAN, MAN, WAN, May, and PAN can be summarised in one word: “distance” or “geography.”
Distance may also be used to distinguish all WLANs and to illustrate how a SAN works by considering several hard drives physically placed in separate locations as a single logical volume.
Internet of Things (IoT) Supporting Technologies (IoT)

Cell phones, coffee makers, refrigerators, microwaves, baby monitors, crock pots, washing machines, headphones, lamps, wearable devices, vehicles, heart-rate monitors, and any other type of device with an IP address that can be controlled over the Internet are all included in the Internet of Things (IoT).
These gadgets can talk with one another and potentially make recommendations or judgments for people depending on the information they gather. When you run out of milk, for example, Internet-connected refrigerators may order it for you!
IoT devices may communicate using a variety of methods.
Bluetooth
Bluetooth creates wireless personal area networks (WPANs) between PCs and peripheral devices like smartphones and printers, as well as input devices like keyboards and mice, consumer electronics like smartphones, and Internet of Things devices like home stereos, televisions, and home security systems.
Although several companies have adopted Bluetooth for this purpose, it was not meant to be a full-featured networking solution.
Bluetooth broadcasts using the frequency-hopping spread-spectrum (FHSS) approach, which allows it to switch between any of the 79 frequencies in the 2.45 GHz range. Bluetooth jumps 1600 times every second from one frequency to the next, making it extremely resistant to interference.
The Bluetooth protocol permits data to be sent at speeds ranging from 723 Kbps to 1 Mbps over a distance of up to 10 metres (about 33 feet).
Bluetooth devices work together in a master/slave system, with one master controlling up to seven active slaves. These roles are automatically assigned and do not need to be configured.
Bluetooth’s WPAN is frequently referred to as a piconet. A piconet may have more than seven Bluetooth slave devices (up to 255) at the same time, but only seven of them can be active at the same time. PARKED DEVICES are slave devices that are not in use.
Visit the official Bluetooth website at https://www.bluetooth.com/ for additional information.
NFC
NFC Near Field Communication (NFC) is a low-speed, short-range technology developed for small-value monetary transactions, among other things. An NFC tag that holds private data and an NFC reader are required for most NFC connections.
The NFC tag is a passive, unpowered gadget. By placing the NFC reader in close proximity to the NFC tag, an electromagnetic induction occurs in the tag, allowing the two devices to interact using just the reader’s power. This is especially useful for NFC-enabled credit cards and other devices that need batteries.
NFC tags have a disadvantage in that they are passive. Any NFC-enabled card in anyone’s wallet or purse may be read by a bad actor with the correct reader, creating a new market for metal-shielded card holders that can block a reader.
While NFC provides minimal encryption, the technology’s security is based on short distances (less than 5cm) and rapid communications (difficult to achieve with a man-in-the-middle attack).
These are okay for basic data transfers when utilising NFC, but they are undesirable for monetary transactions since unscrupulous actors might obtain access to personal information.
NFC is used by all of the main “Tap to Pay” systems, such as Apple Pay and Android Pay, although they build their own security mechanisms on top of it to ensure transaction anonymity.
ANT
ANT+ (Adaptive Network Technique) is a low-speed, low-power networking technology that uses a passive ANT device and an ANT reader, comparable to NFC. ANT was created to address a flaw in existing wireless technologies such as 802.11 and Bluetooth.
Although 802.11 and Bluetooth are excellent wireless technologies, they also need talkative, power-hungry devices. Even while Bluetooth isn’t as power-hungry or as quick as Wi-Fi, it consumes too much power when used with tiny devices like heartrate monitors.
Around 2007, Garmin launched the ANT protocol for low-power sensors that don’t transmit a lot of data and go for long periods of time without transferring data (such as a heart-rate monitor used just once a week). There are also ANT-capable exercise bikes and treadmills on display. (Yes, ANT is really popular in gyms!)
ANT isn’t as well-known as some other networking protocols. Apple smartphones do not have an ANT radio, but around two-thirds of Android devices have. If you wish to utilise an ANT heartrate monitor with your iPhone, for example, you’ll need an ANT USB adapter to communicate with your ANT device.
ANT+ is the most recent version of ANT. ANT/ANT+ is a fantastic protocol that uses very little power and has ample bandwidth for a large number of devices. Because ANT is encrypted using AES, there is no risk of it being hacked (yet).
Z-Wave
Home automation, which involves remotely managing lights, thermostats, cameras, and even a washing and dryer, is a rapidly expanding sector. While wired home automation has been around for a long time, wirelessly linking smart gadgets is a relatively new notion.
There are several barriers to using wireless technologies for home automation. The first is the vast array of IoT gadgets that may be used in a contemporary house, ranging from thermostats to washing machines to power outlets and lightbulbs.
Second, unlike businesses, houses have tiny rooms, tight stairs, and other barriers that make traditional radio-based wifi difficult to use. However, there is a high demand for home automation, and Z-wave is a popular wireless home automation technology.
Another wireless home automation standard, ZigBee, competes with Z-wave. ZigBee is a totally open standard, while Z-wave is a proprietary standard (with an open API for programmers).
Both employ a mesh networking design to let people communicate in their houses, but they also feature hubs that serve as network interconnects.
Infra red
A device that produces coded infrared light and a second device that reads the code and acts on it make up infrared communication. The remote controllers that come with TVs, tuners, and other electrical gadgets are the most ubiquitous infrared devices.
IR blasters may transform any Android phone into a global remote by emulating any IR remote control. There is no danger to your mobile device since these devices simply communicate basic remote-control instructions.
Any IR blaster has the potential to take total control of any device equipped to accept such instructions, making the Android the bad guy. Blocking the IR receivers is the only serious defence.
RFID
RFID Radio-frequency identification (RFID) is similar to NFC in that it employs a tag and reader, but there are a few distinctions. To begin with, RFID isn’t a single standard, but rather a collection of standards that make use of the technology.
Second, various RFID standards use distinct frequencies and protocols. While NFC operates on the 13.56 MHz range, the various RFID standards employ at least six other radio frequencies, ranging from 120 KHz to 10 GHz. The various varied applications and settings that RFID supports need these different bandwidths, which takes us to the following topic.
Third, RFID offers a considerably greater range of uses, ranging from tagging individual pieces in manufacturing to recognising the many components of a deep underwater structure to implanting an RFID tag into your pet. Some aspects are similar to all RFID devices:
Close Proximity Devices (CPDs) communicate within one metre of each other (although a one RFID standard called Ultrawide Band can reach up to 200 metres with powered tags).
Security – The majority of RFID standards have inadequate or no encryption.
Labels – RFID tags are most typically found within labels, which are then attached to whatever component (box, part, or gadget) is being searched.
RFID tags are more simpler to read than NFC tags; with the correct reader, a bad actor can just stroll up to the RFID tag and read it (as opposed to getting within 5 cm). As a result, RFID tags seldom include personally identifying information (PII).
802.11
802.11 The 802.11 committee of the Institute of Electrical and Electronics Engineers (IEEE) supports six WLAN standards: 802.11a, 802.11b, 802.11g, 802.11n…and the most recent and best, 802.11ac and 802.11ad.
www.ieee802.org/11/ is the official website of the IEEE 802.11 Working Group.
Each of these wireless protocols employs radio communications to connect PCs and laptop computers to the internet through a transmitter/receiver device (transceiver), also known as an access point (AP) or wireless access point (WAP), that sends and receives signals to and from wireless network adapters (see Figure 1.5-13). You may establish coverage over a large amount of floor space by carefully placing a number of transceivers.
Be aware that, like the previously listed technologies, any 802.11 may be used to operate IoT devices such as thermostats and crock pots.
Conclusion
Topologies are diagrams, similar to circuit diagrams in electrical engineering. The topologies of star, ring, mesh, and bus vary in appearance and operation. In terms of networks, some don’t even exist anymore.
There are different kinds of topologies for wired and wireless networks. A hybrid topology is any networking technique that blends a physical topology with a logical structure.
Since the dawn of networking, hybrid topologies have come and gone. Mesh topologies offer many pathways between networks, while partial mesh networks are used to link networks.
Wireless networks need topologies to get data from one machine to another. Using radio waves instead of cables involves somewhat different topologies. Wireless networks may run in one of two modes (compTIA calls them ad hoc or infrastructure): wireless mesh topology or wireless infrastructure.
A storage area network (SAN) is a server that may expose a pool of hard drives as any number of logical discs across the network. Campus area networks are a collection of linked local area networks (LANs) located inside a compact geographic region, such as a school campus or hospital.
Bluetooth creates wireless personal area networks (WPANs) between PCs and peripheral devices like smartphones and printers, as well as input devices like keyboards and mice. The Bluetooth protocol allows data to be sent at speeds ranging from 723 Kbps to 1 Mbps over a distance of up to 10 metres. NFC (Near Field Communication) technology is used by Apple Pay and Android Pay.
The ANT protocol was created to address flaws in existing wireless technologies such as 802.11 and Bluetooth. ANT+ is a low-speed, low-power networking technology that uses a passive ANT device and an ANT reader.
Home automation involves remotely managing lights, thermostats, cameras, and even a washing and dryer. Z-wave is a popular wireless home automation technology. RFID Radio-frequency identification (RFID) is similar to NFC in that it employs a tag and reader.
Third, RFID offers a considerably greater range of uses, ranging from tagging individual pieces in manufacturing to. implanting an RFID tag into your pet. Be aware that any 802.11 may be used to operate IoT devices such as thermostats and crock pots.
Questions
- a network administrator designing a new local area network (LAN) needs to determine the type of cabling and the network topology to implement. Which layers of the Open Systems Interconnection (OSI) model apply to cabling and topology elements?
- Physical and data link layers
- Data link and network layers
- Network and transport layers
- Transport and application layers
Answer: The physical layer defines the mechanical and electrical characteristics of the cables used to build a network. The data link layer defines specific network (LAN or WAN) topologies and their characteristics.
- Which of the following topologies required termination?
- Star
- Bus
- Mesh
- Ring
Answer: 2. In a bus topology, all computers connected to the network via a main line. The cable had to be terminated at both ends to prevent signal reflection.
- Star-bus is an example of a _______________ topology.
- transitional
- system
- hybrid
- rampant
Answer: 3. Star-bus is a hybrid topology because it uses a star physical topology and a bus signal topology.
- Of the topologies listed, which one is the most fault-tolerant?
- Point-to-point
- Bus
- Star
- Ring
Answer: 3. Of the choices listed, only star topology has any fault tolerance.
- What term is used to describe the interconnectivity of network components?
- Segmentation
- Map
- Topology
- Protocol
Answer: 3. Topology is the term used to describe the interconnectivity of network components.