Introduction
The production of value for a company is represented by software development. Software is a vital technical aspect in the current business environment, whether it is a product for sale or a tool utilised by a consumer.
While software may provide value to a company, it can also pose a danger. Risk management can considerably decrease much of this inherent risk throughout the software development process.
Risk management is an essential component of decision-making. It refers to the whole process of discovering, managing, and removing or limiting unpredictable occurrences that might have an impact on system resources.
Risk management includes risk assessment, cost-benefit analysis, selection, implementation, and testing of safeguards, as well as an overall security review.
In the simplest terms, risk management is determining the effect of an unfavourable occurrence and determining what you can do to mitigate that damage as much as you or your management considers necessary.
You may then determine whether or not to act based on your knowledge of risks and outcomes. This technique is not only for top management; it can be used at all levels of action across an organisation, and a multilayer, responsive, risk-based management methodology is necessary to properly manage risks in the company.
Risk management is a skill and a duty that all managers must conduct, whether consciously or unconsciously. Depending on the scale of the project or company, as well as the degree of risk involved, it may be simple or complicated.
For risk management, there are two basic methodologies: qualitative and quantitative.
Risk management is something that all managers, at all levels, must learn to do. The goal of risk management is to increase areas where one has some influence over the result while decreasing areas where one has no control over the outcome or where the cause-and-effect relationship is obscured.
In this blog –
- Examine the many categories of risk.
- Learn the fundamentals of risk management terminology.
- Investigate qualitative risk management techniques.
- Investigate quantitative risk management techniques.
- Examine the many forms of risk controls.
Risk management’s goal is to enhance the future, not to explain the past.
Risk Management Statements
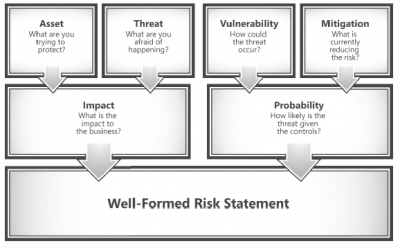
Risk management statements may take many different shapes. A detailed and comprehensive statement may assist minimise misinterpretation induced by an assumption connected with the facts when expressing risk information.
Asset, threat, vulnerability, mitigation, impact, and likelihood are all aspects of a well-formed risk statement.
Risk, Compliance, and Governance
To retain control over a company, management strikes a balance between everyday operations and strategic aspirations and goals by operating according to a set of principles.
This is primarily a risk management exercise for senior C-level personnel and the board of directors. Many mundane operational decisions are delegated to lower levels of management, allowing top executives to focus on risk monitoring and larger-scale adjustments to profit on or mitigate changes in total risk.
The word “governance” has evolved to refer to the total of executive activities related to risk management. Compliance with current rules and regulations is a key part of risk management. As a result, the phrases governance, risk management, and compliance are interchangeable, and the combined term, abbreviated GRC, is used to denote the total of these efforts.
Compliance and Regulations
Management is responsible for ensuring that a broad variety of requirements related to the organization’s business goals and the measures taken to attain them are met.
These demands come from a variety of places: some are contractual, while others are based on policy or strategic ambitions. Others may be defined by the organisation or industry as a process. External needs might also be found in the form of rules or legislation.
The word “compliance” is often used to describe the tasks related with these external regulations. When it comes to actions related to internal requirements, the phrase “conformance” is often employed (organizational policies and standards).
When it comes to GRC activities, compliance and conformance efforts are typically a major concern. Compliance-related activities are often prioritised above conformity.
The priority is based on a number of factors, the most important of which is the penalty associated with noncompliance.
While management measures that are incompatible with compliance may incur internal costs in the form of dissonance, failure to comply with external laws or legal requirements typically results in monetary penalties.
Legal

The act of controlling legal-driven risk aspects is included in governance. Intellectual property and data breach occurrences are two unique legal challenges that pose a major danger to an organisation.
Intellectual property is a company’s most important asset, therefore it must be properly safeguarded. In certain situations, legal action and the courts may be used to acquire this protection.
In other circumstances, however, the legal process has no one against whom it may act. Intellectual property is still lost when it is taken by unknown criminal elements who use the Internet and international boundaries to escape punishment.
In addition to the legal remedies available after a loss, intellectual property requires preventative management.
Additional legal difficulties arise when losses include personally identifiable information (PII). Many states have data breach laws that include procedures for notification and reaction.
When it comes to PII, there are two options. The efforts done to secure the data prior to possible loss are first and essential. Most businesses use encryption as their main technique, and it can fulfill the needs of numerous data breach laws and regulations, including the Payment Card Industry Data Security Specification (PCI DSS).
The expense of complying with data breach notification rules is one of the economic reasons.
Legal problems and penalties play a part in setting the proper balance of actions when top executives assess the alternatives for dealing with risk. Legal ramifications, whether from a failure to comply or a loss, are part of the entire risk equation and should be considered throughout the decision-making process.
Standards
Standards are established standards that specify a set of rules that regulate a certain kind of conduct. There are standards for a broad variety of things, from corporate procedures to results.
Standards come from a variety of places, including government agencies, business groups, and trade associations. The ultimate purpose of standards is to provide a set of guidelines for achieving a certain degree of excellence.
Because the blueprint for designing, building, and managing a system that reflects best practises is the applicable security standards, it is critical for a CSSLP to have a thorough working understanding of them.
Models of Risk Management
Regardless of their definitions, risk management ideas are basically the same, and they demand comparable skills, tools, and techniques. Several models may be used to manage risk as it progresses through its stages.
Here are two models to consider: The first may be used to manage risks in general, whereas the second is designed specifically for software projects.
The goal of risk management is to make the future better, and models may help achieve this goal.
General Risk Management Model
The five-step generic risk management methodology that follows may be used to almost any risk management procedure. These processes will result in a systematic approach to risk analysis and mitigation.
Step 1: The first step is to identify your assets.
Identify and categorise the assets, systems, and processes that need security due to their vulnerability to threats. Choose a categorization that is appropriate for your project.
This categorization allows you to prioritise assets, systems, and processes, as well as assess the costs of mitigating risks. Information may be included in assets, with certain data pieces needing greater protection than others.
Information criticality in relation to the enterprise’s business goals is the most important aspect to consider when assessing value. When assessing value, it’s critical to consider the whole picture, since the location of the breach doesn’t matter from a risk standpoint.
Step 2: Threat Evaluation
Following the asset identification, you must determine the risks and vulnerabilities connected with each asset, as well as the probability of their occurrence.
Vulnerabilities exist in everything; one of the keys is to look for exploitable flaws. Any scenario or occurrence that has the potential to damage an asset is considered a threat.
There is a lot of literature on common software flaws (CWE from mitre.org), the SANS Top 25 list, the OWASP Top 10 list, and so on. These vulnerability lists are a great place to start.
Despite the fact that these difficulties are well-known, they usually go unnoticed, resulting in serious consequences.
Step 3: Quantification and Determination of Impact
An effect is the financial loss incurred when a danger is identified and exploited. There are two types of impacts: physical and intangible. A palpable effect causes monetary loss or bodily harm.
Assigning a financial value to an intangible influence, such as an impact on a company’s reputation, may be challenging.
Step 4: Control Design and Evaluation
This stage determines which controls should be implemented to reduce the risks. Controls (also known as countermeasures or safeguards) are meant to reduce vulnerabilities to a tolerable level, hence decreasing risk. (Control, countermeasure, and safeguard are all regarded synonymous in this book and are used interchangeably.)
Actions, devices, and processes may all be used as controls. The NIST SP 800-53 series contains a complete set of software controls.
Step 5: Residual Risk Management
Recognize that no risk can be entirely removed. A residual risk is a danger that persists after safeguards have been implemented. In this stage, you examine residual hazards in order to determine where more controls are needed to further decrease risk. To establish a superior defensive posture via defence in depth, many controls may be used.
Software Engineering Institute Model
The Software Engineering Institute is a government-funded research and development facility tasked with establishing approaches to decrease software engineering risks.
SEI utilises the following technique to manage risk in software projects (SEI, Continuous Risk Management Guidebook [Pittsburgh, PA: Carnegie Mellon University, 1996]).
Although the SEI language differs significantly from that of the general model, the connections are clear, and either model may be used to manage risk.
- Identify – Examine the system, noting any possible dangers.
- Analyze – Convert the risk data you’ve collected into information you can utilise to make choices with. Evaluate the hazards’ effect, likelihood, and time duration. Each risk should be classified and prioritised.
- Plan – Examine and assess the risks before deciding what steps to take to reduce them. Put the strategy into action.
- Track – Keep an eye on the dangers and the measures for mitigating them. Trends may offer information that allows plans and contingencies to be activated. Review on a regular basis to track progress and identify new threats.
- Control – Make any necessary adjustments to the risk reduction strategies. As needed, correct goods and procedures. Changes in corporate practises, as well as poor plans and risks that become issues, may necessitate changes in plans or actions.
Model Application
The general model and the SEI model outline stages that may be utilised in any risk management approach, general or software. These models may be used on any project or programme, regardless of how basic or sophisticated it is. There is a link between project scope and risk exposure, with risk increasing as the scope of the project grows.
Risk management terms
Risk management is a distinct field with its own lingo. If you wish to speak with individuals in this technical field, you’ll need to know these terminology. The words are arranged into groupings that are connected to one another.
Risk management Risk management refers to the process of recognising threats and vulnerabilities, as well as their possible consequences, calculating the costs of mitigating such occurrences, and choosing which activities are most cost-effective for mitigating these risks.
Risk assessment Risk assessment is the process of studying an environment to identify risks (threats and vulnerabilities) and mitigating measures in order to estimate the effect of an occurrence on a project, programme, or company (quantitatively or qualitatively). It’s also known as risk analysis in certain cases.
Vulnerability Any feature of an asset that may be exploited by a threat to cause damage is referred to as a vulnerability. If you haven’t implemented fixes to remedy a cross-site scripting (XSS) problem on your website, for example, your system has a security vulnerability.
Impact When a threat exploits a vulnerability, the impact is the amount of money lost. An XSS tool is used by a malevolent hacker (the threat) to infiltrate your unpatched website (the vulnerability), obtaining credit card information and using it illegally. The credit card issuer takes legal action against your business in order to recoup the damages caused by credit card theft (the impact).
Qualitative risk assessment The process of subjectively estimating the effect of an occurrence on a project, programme, or company is known as qualitative risk assessment. The qualitative risk assessment is generally completed using expert opinion, experience, or group agreement.
Quantitative risk assessment The process of objectively estimating the effect of an occurrence on a project, programme, or company is known as quantitative risk assessment. Metrics and models are often used in quantitative risk assessment.
Single loss expectancy (SLE) The single loss expectancy (SLE) is the monetary loss or impact of each occurrence of a threat.
Exposure factor Exposure factor is a measure of the magnitude of loss of an asset. When calculating single loss expectancy, this term is used.
Conclusion
Risk management is an essential component of decision-making. It refers to the whole process of discovering, managing, and removing or limiting unpredictable occurrences. Risk management includes risk assessment, cost-benefit analysis, selection, implementation, and testing of safeguards, as well as an overall security review.
The word “governance” has evolved to refer to the total of executive activities related to risk management. Failure to comply with external laws or legal requirements typically results in monetary penalties.
The phrase “compliance” is often used to describe the tasks related with these external regulations. Legal risks are part of the entire risk equation and should be considered throughout the decision-making process.
The cost of complying with data breach notification rules is one of the economic reasons for failing to comply. Several models may be used to manage risk as it progresses through its stages. Identify and categorise the assets, systems, and processes that need security due to their vulnerability to threats.
Vulnerabilities exist in everything; one of the keys is to look for exploitable flaws. Assess risks and determine which controls should be implemented to reduce the risks.
The general model and the SEI model outline stages that may be utilised in any risk management approach. There is a link between project scope and risk exposure, with risk increasing as the scope of the project grows. These models may be used on any project or programme, regardless of how basic or sophisticated it is.
