Introduction
As an information security expert, may consider security to be the most critical factor, the truth is that security is a business enabler, not a business driver.
As a result, security rarely adds value to the bottom line. A lack of security or a security flaw, however, might have a negative impact on the bottom line.
Because security is a business enabler, the company sets the criteria for what is critical and how it will be protected.
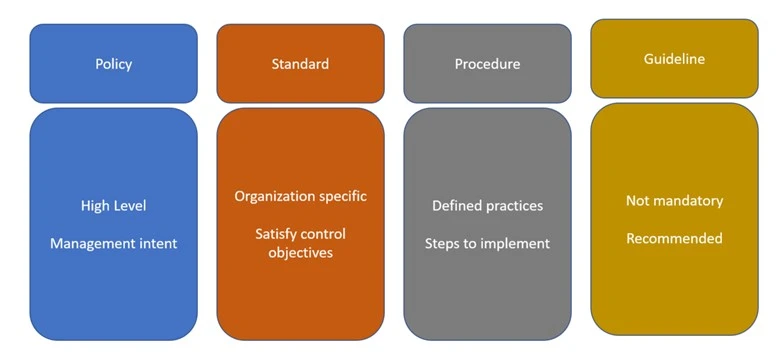
It accomplishes this by enacting policies. Following the creation of policies, standards are developed based on those policies.
Procedures are the closest to where the work is really done. These are created in accordance with the standards.
Security Policies
A security policy is a declaration of intent about a company’s resources.
It specifies what a corporation perceives to be security—what resources must be safeguarded, how resources must be used properly, and how resources can or should be accessible.
Because policies are lines that management draws, they are critical to good company governance. As a result, having management define the tone and direction is not only a good idea but also a requirement.
The stakeholders in the business—individual owners or shareholders—have an obligation to management and the board of directors.
Security policies are significantly more than just outlining key resources; they also create employee expectations.
For example, many organisations have an acceptable usage policy. This is about establishing what users are allowed and not allowed to do.
Any violation of this policy by an employee is usually grounds for disciplinary action or termination, depending on the severity of the offense and the impact on the company.
Of course, not every policy is directly related to users and their actions. Other security rules may be geared toward information technology or information security personnel.
The goal of the security policies
Keep in mind that the confidentiality, integrity, and availability of information resources should be the primary aims of the security policies.
These are the characteristics that a security policy should consider. All information resources should be kept confidential, have integrity, and be accessible within the business’s constraints.
This isn’t to say that all information resources should always be secure, reliable, and accessible. Different information assets will have varying levels of confidentiality, and not all data must be accessible at all times.
This is also what security policy is for: to assist classify and prioritise the organization’s information assets.
Not all information resources are stored as bits and bytes on computers. One aspect of policy that should always be considered is how human resources will be managed.
Human resources should always be a role in information security strategy, especially when it comes to protecting against natural catastrophes and other occurrences that could be physically dangerous as well as impact information assets.
Regular reviews of policies are necessary. They’re high-level enough that they shouldn’t change every time a new set of technologies becomes available, but they should alter as the threat landscape evolves.
As information resources and threat agents evolve, rules may need to adapt to keep up. Any policy change would have to be approved by whatever management structure is in place—business owners, board of directors, and so on—because this is a matter of corporate governance.
Remember that all security policies are high-level. They don’t go into detail about how policies should be executed.
You’re too close to the ground if you’re looking at security policies and starting to consider operational implications and how the administrator would manage the policy.
You’re also considering what should be long-term rather than something unique to a given period of time.
This suggests that the policy excludes technology and solutions. Those components will be handled by other sections of the information security programme.
Security Standards
The first priority is security policy. Subpolicies that cascade down from top-level security policies may also exist.
So that the high-level policy does not become lost, the sub policy should relate to the main policy. Security standards, on the other hand, are found below the policy level.
A standard is a set of guidelines for implementing policies.
The standard begins by describing how we move from statements of intent to implementation, so we begin at the top of the policy and work our way down.
Standards bodies administer and maintain sets of standards that provide guidance to organisations.
NIST has a set of standards, which are detailed in various special publications. ISO 27001 and ISO 27002 are standards maintained by the International Organization for Standardization (ISO).
Other standards publications, depending on where you are in the world, maybe applicable to you.
Consider a policy that stipulates that all systems must be kept up to date. You might have standards for desktop computers, server systems, network devices, and any embedded device in order to move closer to implementing that policy.
Because the criteria for each of those device kinds may vary, the standards for them may also vary.
Desktop computers may simply be expected to accept any updates as they come, with the idea that any potential outage would be rapidly resolved if only a few users’ PCs were affected.
Servers, on the other hand, would be in place to provide service to clients and may potentially affect income. Because of this, the standard may be different.
The standard, which is still focused on how to achieve the policy’s goal, may state that a quality assurance process is required before patches can be released.
In terms of acceptable outages, the service level agreement (SLA) for certain server systems may be radically different.
The server system standard may differ from the desktop system standard, although both are created to support the high-level policy of keeping systems up to date.
To make the policy relevant to operational employees, the standard would specify anything that was vague (what does “up to date” mean?).
The standards are still high-level in the sense that they provide requirements for how policies should be executed. These conditions must still be fulfilled.
Security Procedures
Procedures are how the standard is put into action. These give specific instructions on how the criteria are met at a very detailed level.
This can be performed by providing step-by-step directions on how to complete the task. Because numerous organisations may be involved in implementing the standard, there may be multiple methods for each standard.
You can understand how high-level instructions like that in a policy would be unlikely to be touched frequently.
Policies are reviewed on a regular basis, but if they are properly thought out and drafted, the time it takes for them to change might be measured in years.
However, standards may need to be changed more frequently. Standards would be revised as information assets changed. Any change in technology within the company may necessitate a standard update. Procedures will almost certainly alter more frequently.
Procedures will change to meet changes in the company’s organisations or responsibilities. A good procedure would also include feedback loops so that it could be changed on a regular basis to improve efficiency.
Any change in automation would necessitate modifications in procedures. As we progress through each layer of the security programme, the outcome is increasingly frequent updates as we approach closer to particular implementation and administration processes.
Security Guidelines
security guidelines can vary depending on the type of organization or business. However, some general security guidelines that are often recommended include developing a security policy, implementing security controls, and conducting regular security audits.
Guidelines differ from standards in that they do not always have to be followed. Rather, they are recommendations for how policies should be executed. A guideline may provide information about best practises in the hopes that they will be followed.
Examples of security guidelines:
1. Implement a security policy: A security policy is a document that outlines an organization’s security procedures and controls. It should be reviewed and updated on a regular basis.
2. Implement security controls: Security controls are measures that are put in place to protect assets and minimize risks. They can include things like access control measures, firewalls, and intrusion detection systems.
3. Conduct regular security audits: Security audits help to identify weaknesses and vulnerabilities in an organization’s security posture. They should be conducted on a regular basis by an independent party.
Questions
What is in a security policy?
A security policy typically includes a statement of the organization’s security posture, as well as the rules and procedures for employees, contractors, and third parties.
What are 4 types of security policies in Cyber Security?
-Preventative: Policies and procedures that are put in place to deter potential threats.
-Detective: Policies and procedures designed to detect possible security breaches.
-Corrective: Policies and procedures that are put in place to correct any security vulnerabilities that have been exploited.
-Compensatory: Policies and procedures that are put in place to minimize the impact of a security breach.
What is the main purpose of a security policy?
The main purpose of a security policy is to protect an organization’s information assets.
What are the five components of a security policy?
- confidentiality,
- integrity,
- availability,
- authenticity,
- non-repudiation.
What is a good security policy?
A good security policy is one that is tailored to the specific needs of an organization and that takes into account the type of information that is being protected. The policy should be clear and concise, and it should be reviewed and updated on a regular basis.
List of cyber security policies
1. Access Control Policy
2. Authentication and Authorization Policy
3. Data Classification and Handling Policy
4. Information Security Policy
5. Physical and Environmental Security Policy
6. Systems and Network Security Policy
7. Vulnerability Management Policy
8. Business Continuity and Disaster Recovery Policy
9. Compliance Policy
What is the best security standard?
There is no one best security standard. Different standards exist for different types of organizations, and the best security standard for a given organization depends on that organization’s specific needs. Some common security standards include the ISO 27000 series, the NIST Cybersecurity Framework, and the CIS Controls.
Security standards list of examples
International Standards
1 ISO/IEC 27001 and 27002
2 ISO 15408
3 IEC 62443
4 ISO/SAE 21434
5 ETSI EN 303 645
National Standards
1 NERC
2 NIST
3 FIPS 140
4 Cyber Essentials
5 BSI IT-Grundschutz
Industry-specific Standards
1 PCI DSS
2 UL 2900
Source: https://en.wikipedia.org/wiki/IT_security_standards
What are security standards?
Security standards are a set of guidelines that organizations use to ensure the safety of their information and systems. These standards can be developed by an external body or by the organization itself.
Types of security standards
There are several types of security standards, including:
* Anti-virus software standards
* Application security standards
* Cloud security standards
* Cryptographic algorithm standards
* Data security standards
* Hardware security standards
* Information security management standards
* Network security standards
* Physical security standards
* Security architecture standards
* Web application security standards
* Wireless security standards
Explain Procedures vs Standards
A procedure is a specific set of instructions that must be followed in order to complete a task, while a standard is a guideline that suggests a certain way of doing things but does not require it.
What is the purpose of security procedures?
The purpose of cybersecurity procedures is to protect computer networks and electronic information from unauthorized access or theft.
Security procedures examples list
1. Establish and maintain an information security program
2. Develop and implement security policies and procedures
3. Train employees in security awareness and procedures
4. Select and implement security controls to protect information assets
5. Monitor and evaluate the effectiveness of security controls
6. Respond to security incidents in a timely and effective manner
7. continuously improve the security program
What are the types of security procedures?
There are many types of cybersecurity procedures, but some of the most common include firewalls, intrusion detection and prevention systems, data encryption, and access control.