CEH Preparation Series: Cyber security Policies, Standards, and Procedures
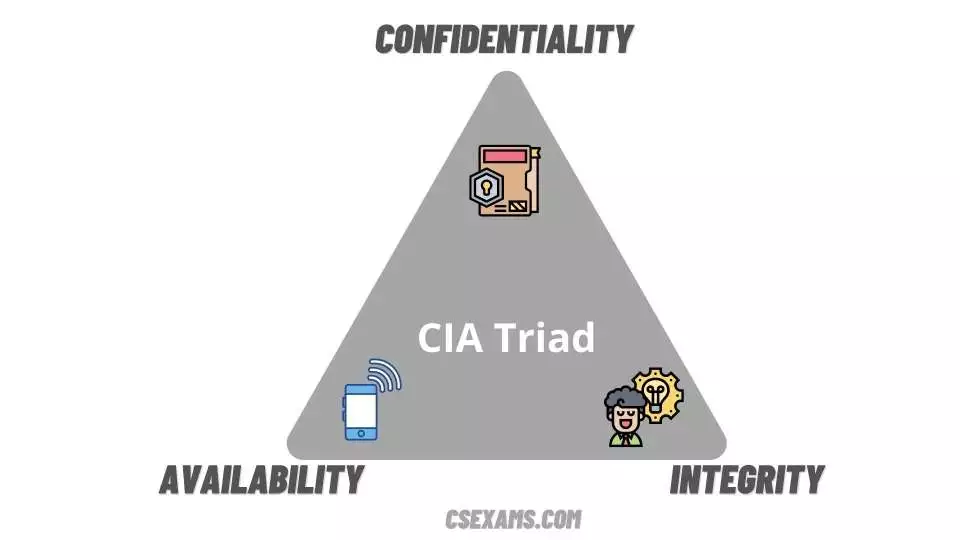
Introduction As an information security expert, may consider security to be the most critical factor, the truth is that security is a business enabler, not a business driver. As a result, security rarely adds value to the bottom line. A lack of security or a security flaw, however, might have a negative impact on the […]
CEH Preparation Series: Cyber security Policies, Standards, and Procedures Read More »