Introduction It’s critical for professionals to stay current on the newest technologies, methodologies, and best practises in the rapidly changing […]
Introduction The Certified Information Security Manager (CISM) certification is a globally recognized credential that signifies expertise in information security management. […]
If you’re looking to prepare for the Certified Information Security Manager (CISM) exam, then this blog and free resources on […]
Introduction If you’re just getting started in the world of cybersecurity, you probably have a lot of questions. You […]
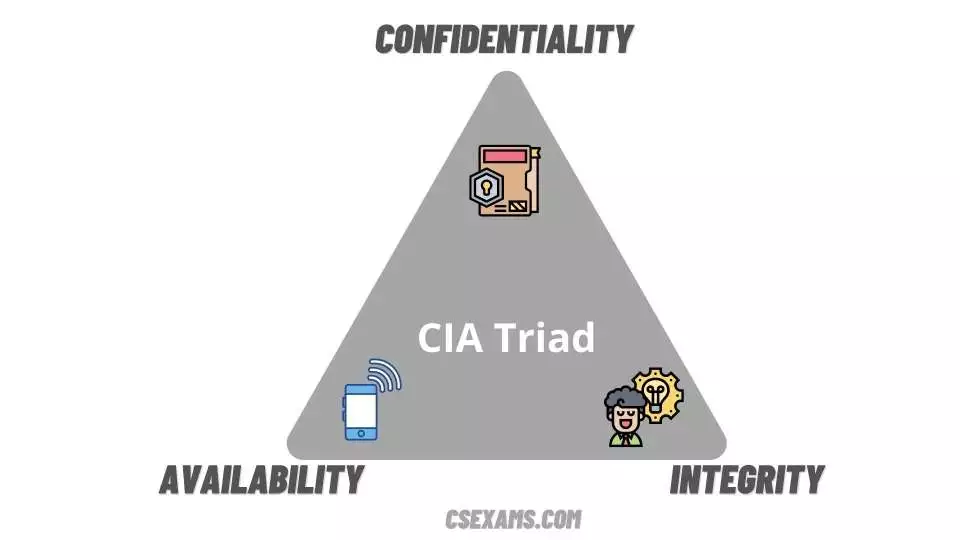
Introduction As an information security expert, may consider security to be the most critical factor, the truth is that security […]
Introduction Organizations typically devote a significant amount of effort and money to attack defenses and mitigations. The planning and implementation […]
Introduction Linux is a UNIX-like computer operating system developed and distributed under the free and open source software concept. The […]
Introduction Linux servers are used in local network environments to provide simple network services, besides running large Internet web and […]
Android secret codes are a set of codes that can be used to access various hidden features and settings in […]
Introduction CISSP is one of the most renowned certifications in cyber security. In this post, I will talk about the […]
What is the darknet, and what are some awesome darknet sites? In this video we list some of the useful […]
Cybersecurity professionals are in high demand in today’s job market. Many candidates try to stand out by obtaining a cybersecurity […]