Introduction
Organizations typically devote a significant amount of effort and money to attack defenses and mitigations. The planning and implementation of these defenses are guided by a few basic concepts.
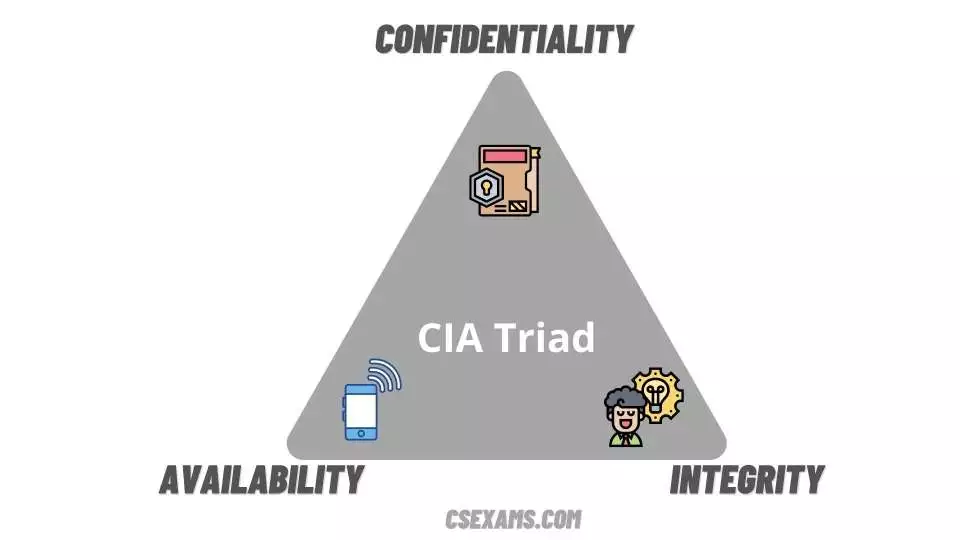
You must comprehend what information security entails, as well as which events fall into the security category. The trio, often known as the CIA triad, is a collection of ideas. The triangle is the main starting point for learning about information security in general.
Any information system attack will compromise one, two, or all three of these components. Effective security controls can be created based on which of these components is being compromised the most.
In this blog, we will discuss below topics –
- What are the three principles of the CIA triad?
- Why is CIA triad important for cybersecurity?
- Confidentiality, integrity and availability with examples
- CIA triad attacks
- Parkerian Hexad
- CIA triad questions
What are the three principles of the CIA triad?
The triad is a set of three characteristics or features that determine security. Confidentiality, integrity, and availability are the three aspects.
When designing security plans, each of these characteristics must be considered. Each of them will play a role in defense preparation to varying degrees of prominence.
Each of the three attributes will not be used to the same level in every defense. Some defenses, for example, only affect one property.
Importance of CIA triad
A tester or adversary would try to compromise one of these elements within an organisation in the event of an attack. The CIA trio is a term used to describe these three characteristics.
One explanation for this is that all of the sides of an equilateral triangle are the same length. They have the same worth or weight, which is designed to show that none of the triad’s attributes are more significant than the others.
When it comes to an organization’s overall security posture, they are all equally important. Different situations will emphasize different parts, but when it comes to an organization’s overall security, each is given equal weight to provide a well-balanced strategy.
If any of these attributes is removed or hacked, your organization’s security is likewise jeopardized. It takes all of these characteristics to ensure that you and your data are safe.
Confidentiality in CIA triad
The confidentiality aspect of the CIA triad refers to the measures taken to prevent unauthorized access to information.
Confidentiality in the digital world entails keeping secrets. This, on the other hand, covers a wide range of topics. It entails ensuring that no one has illegal access to data.
To prevent attackers from gaining access to your user accounts, you may need to use strong passwords. It could involve keeping some data offline so that it can’t be accessed remotely. However, using encryption is a common and straightforward approach to establish confidentiality.
What is confidential information?
Some examples of the confidential information could be:
- Passwords
- Financial records
- Medical records
- Intellectual properties
- Trade secrets of the company
- Product information which is yet to be released
Static and dynamic confidential data
When we discuss confidentiality in this context, we should consider it in two dimensions: static and dynamic.
Data that is considered “at rest,” or not moving, would be protected by static. It’s most likely saved on disc and never utilised or altered.
The second category, dynamic, refers to data that is always changing or “in motion.”
When data is sent from one location to another, this is referred to as transmission.
This could include your web browser requesting and retrieving data from a web server. The data is in motion as it is transferred.
It’s the transmission that makes it dynamic, not the fact that it’s being changed, but data being transmitted from one location to another might certainly be changed as a result of user and application interaction.
How is confidentiality protected?
The Secure Sockets Layer/Transport Layer (SSL/TLS) security protocols are utilised when using encryption for web-based communication. Despite the fact that TLS has long since supplanted SSL, it is still referred to as SSL/TLS.
It is, nevertheless, a set of processes for encrypting data, regardless of how it is referred to. Both SSL and TLS describe how to generate encryption keys from known data as well as some partial data sent from one side to the other.
The secrecy of the data is secured since encrypted data cannot be read without a key. This isn’t to imply that encryption provides complete privacy.
If an attacker is able to obtain the key in some means, the data can be decrypted. Confidentiality is obviously jeopardised if the data is decoded by someone who shouldn’t have access to it.
Attacks on encryption techniques, such as cyphers and key exchange algorithms, can potentially affect confidentiality. A successful attack on the encryption, as there have been against many encryption algorithms and standards, will result in the decryption of the ciphertext.
CIA triad attacks : Confidentiality attacks examples
- Brute force attacks like password cracking
- Attacks against encryptions
Example measures to protect confidentiality
- Physical security, such as locks and security cameras
- Restrict access to physical locations where confidential information is stored
- Logical security, such as password protection and encryption
- Limit access to confidential information to authorized individuals
- Use strong encryption to protect confidential information
- Use access control measures, such as passwords and user IDs, to restrict access to confidential information
Integrity in the CIA triad
The integrity aspect of the CIA triad refers to the measures taken to prevent unauthorized modification of information.
We want data to be consistent from the time we supply it to the time it is received, in addition to being confidential.
Furthermore, if we store data, we want it to be intact when we retrieve it. The term “integrity” is used to express this concept.
Why integrity is important?
It is critical to maintain data integrity. It can be harmed in a variety of ways. For starters, data can be tampered with. It’s possible that it’ll be tampered with while in route. On disc or in memory, it can be corrupted.
Data can be corrupted for a variety of causes. In a computer system, defective components can occur, and these bad components can cause data loss or corruption.
You accidentally overwrite a piece of the real document while thinking you’re in the scratch document, and then you save the document you’re working on because you don’t trust autosave. Because crucial parts of the document you’re working on have been changed, this could be deemed a loss of data integrity.
You may not be possible to retrieve the original if you don’t have a backup from which to replace data, and you may not even notice the mistake until the document has been circulated across the workplace with the text containing the mistake. Suddenly, material is being disseminated that is in some manner inaccurate.
How integrity can be compromised?
An attacker can violate integrity by using a man in the middle attack. The attacker intercepts data in transit, modifies it, and then transmits it back.
When you visit a website that uses encryption, you’ll see that a certificate is utilised to provide keying, which means the certificate contains the encryption and decryption keys.
Your browser will generate an error if a certificate has a name that differs from the hostname being visited.
CIA triad attacks: Integrity attacks
- Tampering with data to change its meaning or purpose
- Altering data to evade detection or analysis
- Inserting malicious code into data to corrupt or delete it
- Fabricating data to mislead or deceive
- Using data for unauthorized purposes
- Destroying data to prevent its use
Example measures to protect integrity:
- Physical security
- Tamper-proof seals
- Restrict access to physical locations where information is stored
- Limit access to information to authorized individuals
- Use digital signatures and checksums to verify the integrity of information
- Store information in read-only format
Integrity, it turns out, is a difficult concept to grasp. There are a plethora of situations in which integrity can be abused, and we’ve just scratched the surface. Integrity isn’t just about the data’s content. It could also be the reliability of the information source.
Availability in the CIA triad
The availability aspect of the CIA triad refers to the measures taken to ensure that information is available when needed.
It all boils down to whether or not information or services are available when the user expects them to be.
As with the other attributes, this could be a matter of human error rather than malice. If you keep information on an external drive and then neglect to carry it with you somewhere—work, a client’s site—the files on that drive will be lost.
There wouldn’t be malevolent, but it would still be a lack of availability because you wouldn’t be able to get what you needed when you needed it. You haven’t misplaced the information. It’s still in good condition. It’s just not where you need it to be when you need it. That’s a non-availability breach.
Misconfigurations can lead to availability issues. If you make a change to a service configuration without testing it beforehand, the service may not come back up.
This can be highly difficult in production, especially if the failure of the service isn’t obvious. When the setting causes the service start to fail, some services will appear to have restarted. Even if the modification is just rolled back for a short time, there is a chance that users of the service will be unable to execute the functions they expect.
How availability can be compromised?
A denial of service (DoS) attack prevents genuine users from accessing a service, making it unavailable to them. Attackers can overwhelm a service by flooding it with requests, making it impossible for it to answer.
A reasonable request would struggle to break through the noise, and even if it did, the service might not be able to answer.
DoS assaults have been around for decades, but due to changes in available bandwidth and other technological advancements, the attacks have had to evolve to keep up with the changes in technology and bandwidth.
CIA triad attacks: Availability attacks
- A Denial of Service (DoS) attack is an attack meant to render a machine or network resource unavailable to its intended users.
- An attacker could try to flood a server with requests in an attempt to overload it and take it offline.
- A Distributed Denial of Service (DDoS) attack is similar to a DoS attack, but it involves multiple machines attacking the same target. This can make it much harder to defend against, as the attack is coming from multiple sources.
- An attacker could also try to exploit vulnerabilities in the software running on a server in order to take it down. For example, they could try to find a way to crash the server or make it consume all of its resources so that it can no longer function properly.
Example measures to protect the availability
- Store information in multiple physical locations
- Replicate information across multiple servers
- Back up information regularly
- Use redundant power supplies and other hardware
Parkerian Hexad
Not everyone thinks three qualities are enough to cover the entire scope of information security. Donn Parker added three more homes to the initial three in 1998. These aren’t regarded standard because there’s some controversy about whether or not the additional characteristics should be separated. The following are the three extra qualities that Parker believes are required:
Possession is the state of having something (or Control)
If you handed the external drive stated previously to a buddy by mistake, thinking you were returning it to them, the drive would be in their possession. The data on the drive would not be susceptible to a breach of confidentially if the buddy never plugged it in to look at it. However, because the drive is no longer under your control, it is no longer available to you, resulting in a loss of availability. This is one of the reasons why this attribute isn’t included in the fundamental triad, despite the fact that it is a significant distinction.
Authenticity
Non-repudiation is a term used to describe this. The principle of authenticity is that the data or document’s source is exactly what it claims to be. When you digitally sign an email message, for example, the recipient can be sure it came from you since the message includes your digital signature, which no one else should have. In truth, all we know is that your key was used to sign the message. Your key could be used without your knowledge if it was stolen or handed away. Authenticity refers to ensuring that when you receive a piece of data, no matter what it is, it comes from the source it claims to come from.
Utility
Let’s pretend you have the same external drive we’ve been discussing. It’s been many years since I last looked at it, and it’s been tucked away in a drawer for quite some time. It’s only a matter of getting there. Because they were separated, there is no cable with it. You don’t have the cable any longer, and your computer’s interfaces have all changed since the last time you used it. You now have data, but it is useless. It serves no purpose.
While these features highlight distinct thoughts that are crucial to consider, the scenarios might also be categorised under the three CIA triad properties. Availability may be divided into possession and utility scenarios, while integrity can be divided into authenticity. After all, if the source of a piece of data is claimed to be one thing but isn’t, the data’s integrity is tainted. The Parkerian hexad provides specific situations rather than the CIA triad’s wider notions. The hexad may be more useful for you than the triad if you find it easier to separate them from the others when you consider what security entails and what occurrences are security-related.
CIA triad questions
Q1. Which of the below lists the main security goals and objectives?
A. A network’s border perimeter
B. The CIA Triad
C. A stand-alone system
D. The Internet
The Correct Answer is B. The CIA Triad, or confidentiality, integrity, and availability, are the three fundamental goals and objectives of security.
Q2. Threats against which of the following are used to evaluate vulnerabilities and risks?
A. One or more of the CIA Triad principles
B. Data usefulness
C. Due care
D. Extent of liability
The Correct Answer is A. Threats to one or more of the CIA Triad principles are used to analyse vulnerabilities and risks.
Q3. Which of the following is a CIA Triad concept that ensures authorised individuals have timely and uninterrupted access to objects?
A. Identification
B. Availability
C. Encryption
D. Layering
The Correct Answer is B. Authorized subjects have timely and uninterrupted access to things, which is referred to as availability.
Q4. Which of the following does not constitute a breach of privacy?
A. Stealing passwords
B. Eavesdropping
C. Hardware destruction
D. Social engineering
The Correct Answer is C. Hardware destruction jeopardises availability and, potentially, integrity. Capturing network traffic, collecting password files, social engineering, port scanning, shoulder surfing, eavesdropping, and sniffing are all examples of confidentiality violations.
Q5. Which of the following factors affects confidentiality?
A. Accountability
B. Availability
C. Nonrepudiation
D. Integrity
The Correct Answer is D. Confidentiality cannot be sustained without integrity.